Malware Analysis Part 1.1 : Basic Static Analysis
I've decided to improve my previous entry about Malware Analysis 1. I've learnt several tools and techniques that obtained from ENISA training sheets and Sam Class. Thanks ENISA and SAM for a good stuff!
So I just used malicious sample from Practical Malware Analysis Lab for this analysis.
-----------------------------------------------
Detecting and Unpacking Packers
-----------------------------------------------
-----------------------------------------------
Detecting and Unpacking Packers
-----------------------------------------------
This is a techniques that has been used by malware author to obfuscate or evade from AV detection. First, upload the malware sample into PEid:
Indicates that the malware was using UPX packer. Then use ExeInfo PE for further verification.
Confirmed that
malware was using UPX and use advance scan by clicking '>' button.
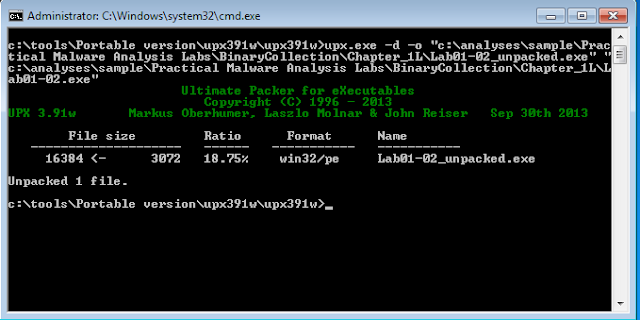
Then
unpacking the malware using UPX
Re-analyzed the sample by using PEiD. Its
recognized the sample as Microsoft Visu C++ file.
-----------------------------------------------
Strings Analysis
-----------------------------------------------
Searching through
strings can be simple way to get hints about the functionality of a program by observe multiple Win .
For instance, if the program accesses a URL, we will see the URL stored as a string in the program. Or if the program connects to C&C, the
IP address will appear in the strings.
It can be done by upload
the unpacked malware and click Go button to extract strings.
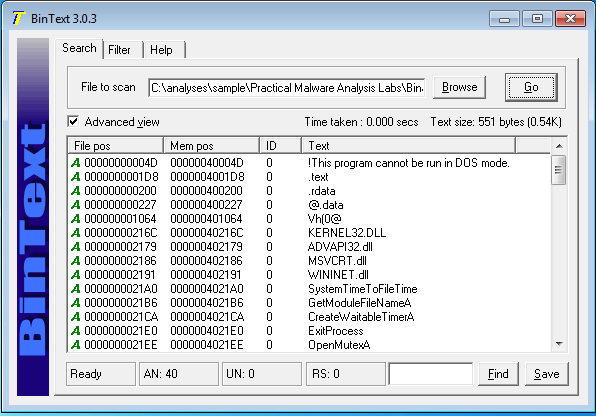
The import from
kernel32.dll and msvcrt.dll are imported by nearly every program. Advapi32.dll
(CreateService) indicates that the code creates a service.
Then ,the imports from
wininet.dll indicates this code connects to the Internet
Notice that,
http://www.malwareanalysisbook.com which probably link opened by
InternetOpenURL. And MalService could be the name of the service that is
created. Based on above
analysis, found the several indicators this malware will connect to Internet
and create suspicious services.
-----------------------------------------------
Examining PE Files
-----------------------------------------------
PE file format stores
interesting information within its header. Use PEview tool to browse through
the information.
IMAGE_OPTIONAL_HEADER and the address
of the entry point (EP) will be used for the next step to determine in which
PE section the entry point is located.
--------------------------------------------------------------------
Exploring Dynamically
Linked Functions and Import Table Analysis
--------------------------------------------------------------------
Dynamic linking is the most common and interesting in malware analysis. When libraries are dynamically linked, the host OS searches for the necessary libraries when the program is loaded. When the program calls the linked library function, that function executes within library.
By uploading sample into Depedency Walker, we noticed that the sample was import 4 DLL [kernel32.dll, advapi32.dll, msvcrt.dll and wininet.dll]. For example, the program import the function InternetOpenUrl, it indicates that it parses the URL string, establishes a connection to the server, and prepares to download the data identified by the URL. Alternatively, we can use CFF Explorer to analyze Import Address Table (IAT).
The imports from
Kernel31.dll shows that this program or file can manipulate processes
(ExitProcess) and files (SystemTimeToFileTime and GetModuleFileNameA).
The imports from
Advapi32.dll shows that the program creates a service (CreateServiceA).
Meanwhile, the
imports from Wininet.dll tell us the program will connect to Internet once the
host infected.
-----------------------------------------------
Searching for embedded objects
-----------------------------------------------
Malware might
sometimes contain embedded objects outside of the resources section. Exeinfo PE
tool has a special function allowing to scan any file for embedded objects in
popular formats such as PE files, MSI files, Word documents, images, etc.
Using Exeinfo PE and
clicking on the Rip button. Then choose what type of object Exeinfo PE should
search for, or choose the I’m hungry for Ripping option to search for
all known file types.
If any embedded
objects are be found they will be saved to the same directory in which the
analyzed sample resides.
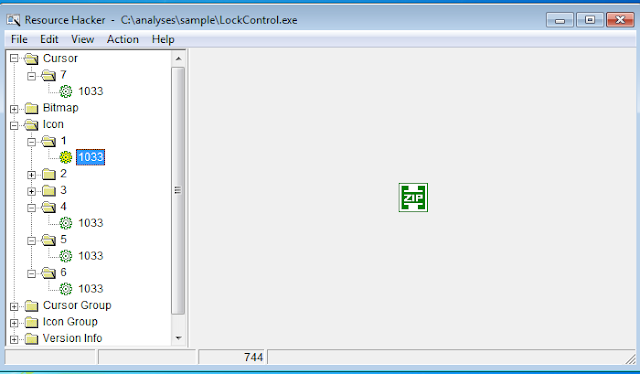
In this binary
sample, there are 2 icons and 2 zip files found.
-----------------------------------------------
Viewing the Resource
Section
-----------------------------------------------
Then use Resource hacker tool to browse the .rsrc section. By using this tool, we will see the strings, menus, icons and etc.
Then use Resource hacker tool to browse the .rsrc section. By using this tool, we will see the strings, menus, icons and etc.
The icon section
lists images shown when the executable is in the listing.
The version Info
section contains a version number and often the company name and a copyright
statement.
* The last 2 exercise I've used differen sample called LockControl.ex_.

















Comments
Post a Comment