Email Header Analysis
If we go to the Spam mails, we will find an email for instance the email that sent by banks. Then it required us to update user credentials such as username and password. That email usually was contained a link so that once the user clicked, it directed to the update page. It was a phishing or fraudulent email that sent by attacker to steal the credentials.
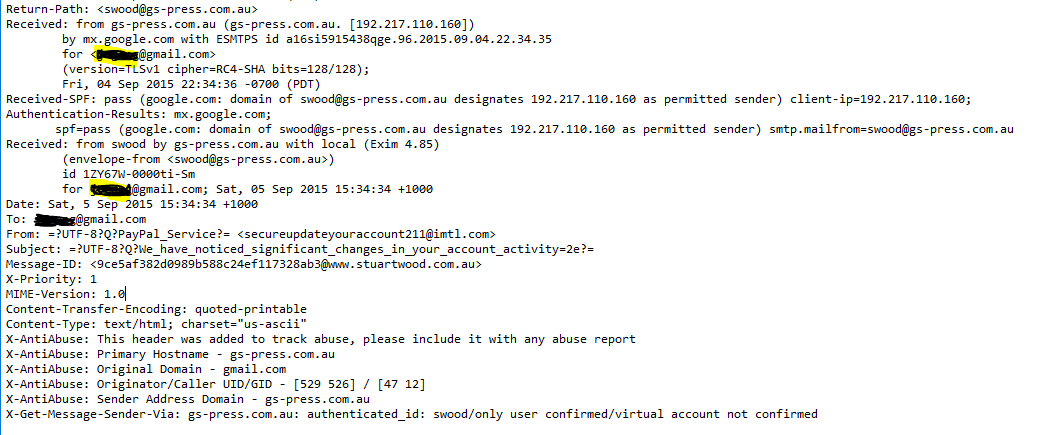
There are several types of phishing attacks but for this entry, I would like to talk about how to analyze the email header. If you are using Gmail, we can get the email header by click Show Original. An email consists of 3 elements: the envelope, the header(s), and the body of the message. Sample fraud email:
Email Header
---------------
The header contains the "name" and "address" of the sender, recipient and anyone who is being copied, the "date" and "time" the mail is sent and the "subject" of the mail. The header exists mainly for the computer to route mail to you. The "received:" item indicates the mailers. It shows what mailers the mail is routed through before it goes to the recipient. Usually, over the internet, the mail will go through several mailers before it finally reaches the recipient. This information will help in tracing the source IP address of the sender.
How to read an email header?
---------------------------------
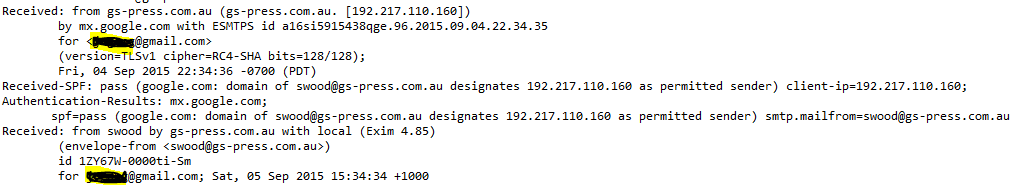
Email headers should be read from bottom to top. Sample header as follows:
Line by line analysis
----------------------------
The Return-Path line mean the address in which the reply for this mail will be sent to. This is the same as "Reply-To:”. Attackers use the different real address to deceived the target.
The preceding lines were the routing information which told where the mail went and the time it arrived to the respective mailer. In order to follow the flow, they had to be read backwards. So, the particular mail originated from gs-press.com.au and mailed to mx.gmail.com. Further, it went to xxx@gmail.com which was the recipient's Internet host. So, if your mail bounced, this part
in the header showed how far the mail went and which machine rejected it.
The message-Id line was intended mainly for tracing mail routing and uniquely identified each mail.
The 'From' line showed who sent the mail and his/her email. 'From' information can be easily be faked/forged.
The 'To' line listed the email address/es of the recipients of the mail. There might be also a Cc line which listed all the people who received copies of this mail. This address could also be a hidden list of emails; thus your email may not appear in here even though you received the mail.
The subject line gave some idea of what the mail is about.
The Date line lists the date and time this mail was originally sent. It was sent on the sender's local time zone.
That's all for now. Chow!
There are several types of phishing attacks but for this entry, I would like to talk about how to analyze the email header. If you are using Gmail, we can get the email header by click Show Original. An email consists of 3 elements: the envelope, the header(s), and the body of the message. Sample fraud email:
Email Header
---------------
The header contains the "name" and "address" of the sender, recipient and anyone who is being copied, the "date" and "time" the mail is sent and the "subject" of the mail. The header exists mainly for the computer to route mail to you. The "received:" item indicates the mailers. It shows what mailers the mail is routed through before it goes to the recipient. Usually, over the internet, the mail will go through several mailers before it finally reaches the recipient. This information will help in tracing the source IP address of the sender.
How to read an email header?
---------------------------------
Line by line analysis
----------------------------
The Return-Path line mean the address in which the reply for this mail will be sent to. This is the same as "Reply-To:”. Attackers use the different real address to deceived the target.
The preceding lines were the routing information which told where the mail went and the time it arrived to the respective mailer. In order to follow the flow, they had to be read backwards. So, the particular mail originated from gs-press.com.au and mailed to mx.gmail.com. Further, it went to xxx@gmail.com which was the recipient's Internet host. So, if your mail bounced, this part
in the header showed how far the mail went and which machine rejected it.
The message-Id line was intended mainly for tracing mail routing and uniquely identified each mail.
The 'From' line showed who sent the mail and his/her email. 'From' information can be easily be faked/forged.
The 'To' line listed the email address/es of the recipients of the mail. There might be also a Cc line which listed all the people who received copies of this mail. This address could also be a hidden list of emails; thus your email may not appear in here even though you received the mail.
The subject line gave some idea of what the mail is about.
The Date line lists the date and time this mail was originally sent. It was sent on the sender's local time zone.
That's all for now. Chow!








Comments
Post a Comment